Yes, this post was created with AI, but I checked its work.
Based on our implementation, here's a comprehensive guide on how to build robust killswitches into your Gainsight rules to prevent data disasters and massive CTA creation incidents.
🎯 Why Killswitches Matter
Imagine waking up to find your rule created 2,000 CTAs overnight because of bad data, or worse - your health scores were incorrectly set to zero because a data source failed. Killswitches are your safety net, providing automated circuit breakers that stop rules when unexpected conditions are detected.
🛠️ Two Main Killswitch Patterns
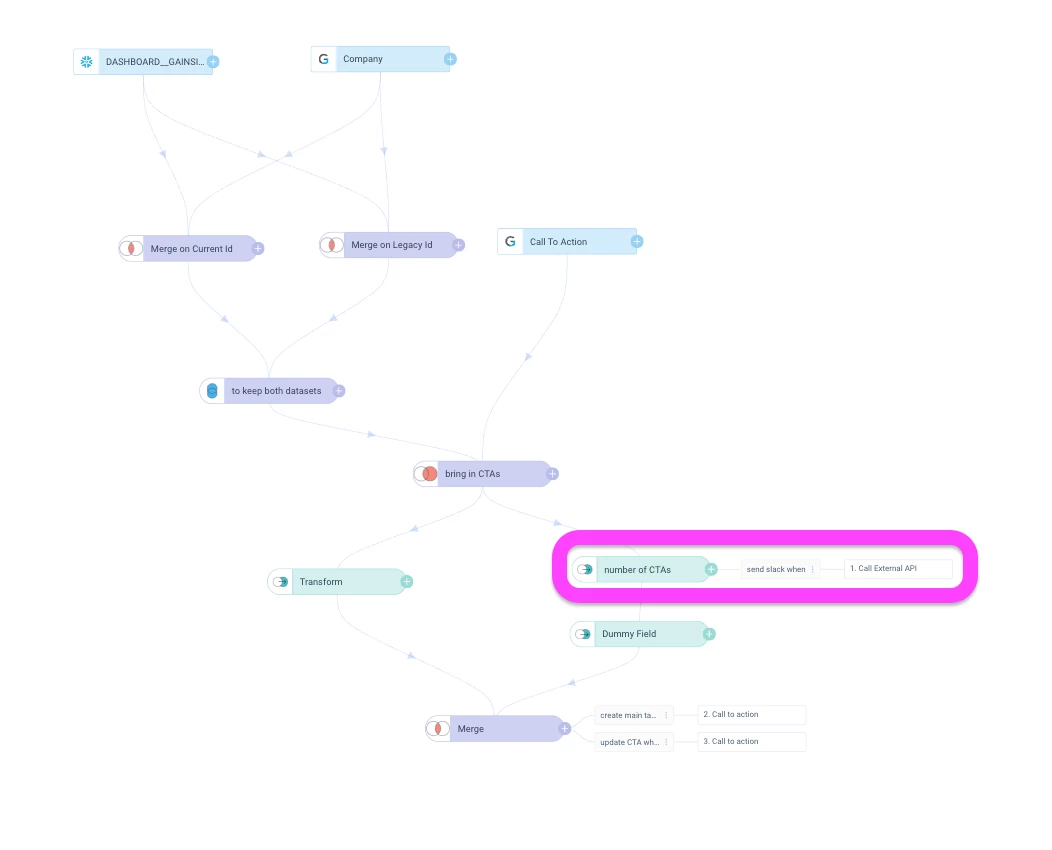
1. Volume-Based: Preventing CTA Explosions
Use Case: Risk CTA creation that depends on external data sources
Implementation:
- Count the number of CTAs that would be created by your rule
- If count exceeds a reasonable threshold (e.g., 100 CTAs), abort the rule
- Send Slack notification to alert your team
Setup Steps:
- Add a Transform step to count the number of CTA records
- Include a Slack notification action for the inverse:
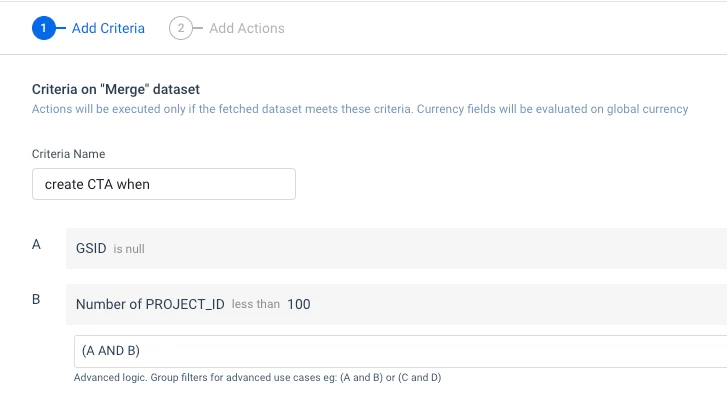
IF Count < [threshold] THEN send Slack notification - Add a filter in the action criteria:
IF Count < [threshold] THEN allow rule - Use a descriptive but professional message (save the fun GIFs for later! 😄)
Benefits:
- Prevents mass CTA creation from bad or missing data
- Gives you time to investigate anomalies without also having to clean up a mess
- Saves on manual CTA cleanup, RCAs, CSM frustrations
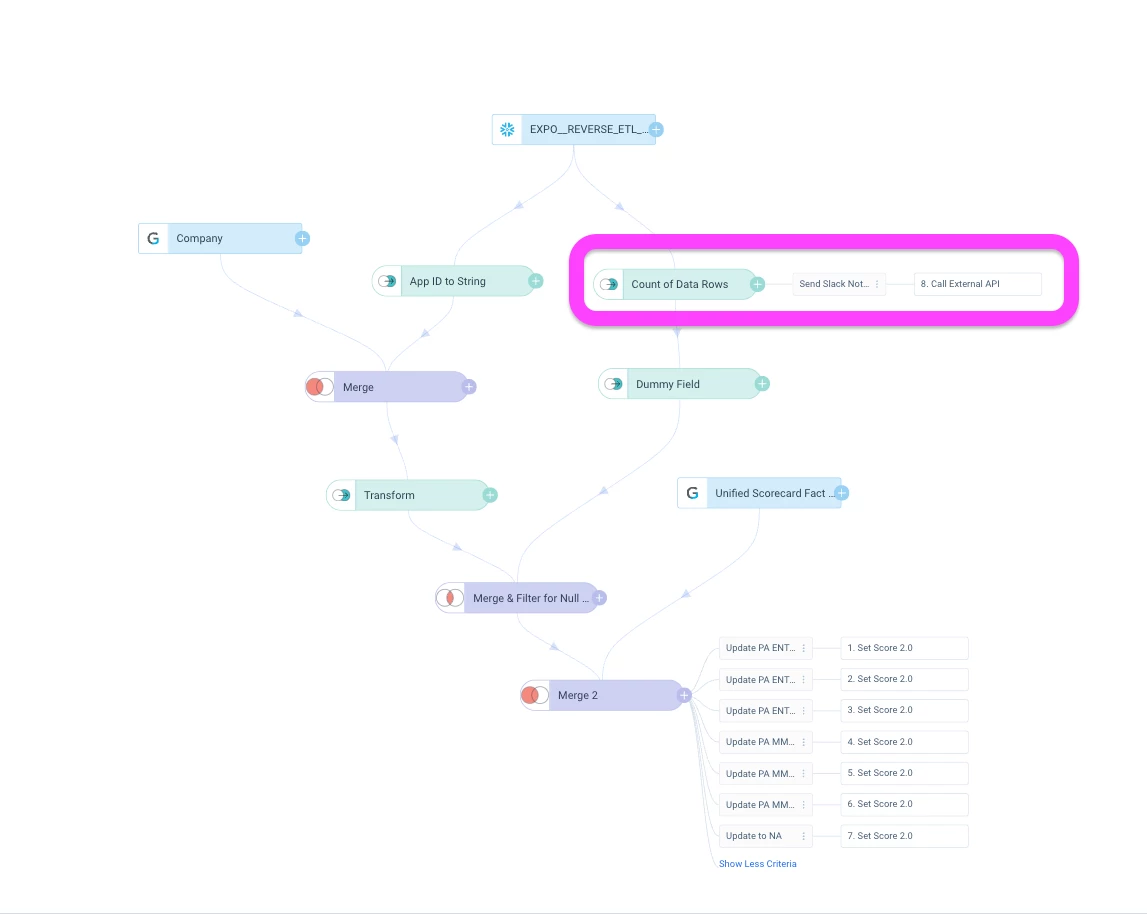
2. Data Validation: Ensuring Data Quality
Use Case: Another way to approach this is by counting up the rows of data you are receiving from external sources. Health score updates or any rule dependent on external data sources where you expect a large volume of data per day.
Implementation:
- Count incoming data rows from your source (e.g., Snowflake)
- If count is below expected threshold, abort the rule, and send a slack message
- Particularly useful for preventing "red" scores during data outages
Setup Steps:
- Count records from your data source in a Transform step
- Set a minimum threshold (based on historical data) and send a Slack message when the count is lower than expected:
IF Count < [threshold] THEN send Slack notification - Add a filter in the action criteria:
IF Count > [threshold] THEN allow rule
Implementation:
- Check for minimum data volume from Snowflake
- If insufficient data detected, stop rule execution
- Alert team via Slack for investigation
🔧 Technical Implementation Tips
Setting Up Slack Notifications
- Create a dedicated Slack channel for rule alerts (e.g.,
#gainsight-alerts) - Use a Slack Workflow paired to Gainsight External Actions to send notifications
- Include key information:
- Rule name and purpose
- Threshold that was exceeded
- Data source involved
- Recommended next steps
🎉 The Warm Fuzzy Feeling
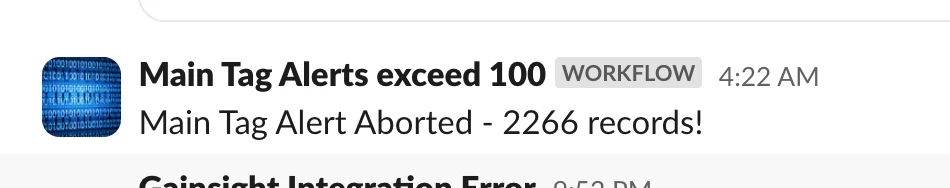
There's nothing quite like getting a quiet alert that your killswitch just prevented 2,000 incorrect CTAs from being created. It's a small victory that prevents a massive defeat!
💡 Pro Tips
- Document everything - future you will thank present you
- Only make changes when you need to - Note that we are comparing our dataset to the scorecard fact and CTAs objects, and only make updates when needed.
- Test failure scenarios in your sandbox environment
- Make alerts actionable - include what to do next
- Celebrate the saves - acknowledge when killswitches work as intended
This approach has saved our team hours of cleanup work and prevented several potential data disasters. The peace of mind knowing your rules have built-in safety mechanisms is invaluable for any Gainsight admin.


